Update 2019-04-04: The use of not encrypted connections to retrieve directions was first reported in 2014 by researchers of the STIC Program of Fundación Sadosky. Source: https://github.com/programa-stic/security-advisories/blob/master/BAComoLLego/README.md
Update 2019-04-10: The Android version of the “BA Como Llego” application was updated on April 5, 2019. The main issues addressed in our blog were solved, however location about the destination searched by the user is still leaked. Moreover, not all communication of the application is encrypted, basic information about phone model, OS, language, and in some cases what topic is searched. The Apple iOS version of “BA Como Llego” has not been updated yet. We have not received any response from the developers to our email in which we detailed the issues reported here.
Update 2019-06-03: On April 23, 2019 Dirección General de Ciencias de la Información responded to our email addressing the issues and said the issues will be fixed. The Android version of the “BA Como Llego” application was updated on April 5, 2019. All of the issues addressed in our blog regarding the Android version were resolved. However, all of the issues in the Apple iOS version of “BA Como Llego” remain.
SUMMARY
In this blog post we report important issues found on the public transport application “BA Cómo Llego” developed by Argentinean Government. A summary of the issues found is:
The application sends the exact location of the users in clear text over the network. Anyone with access to the traffic can know where you are.
Every search done in the app by the user is sent in clear text, leaking the content of the search. Anyone with access to the traffic can know what you type in real time.
Every character typed generates a new request, leaking not only what you type but how you type it. Anyone with access to the traffic may analyze who you are.
This affects iOS application version 5.6.0, and current Android application.
ABOUT THE APPLICATION
“BA Cómo Llego” is an application developed by the Government of Buenos Aires City (“Gobierno de la Ciudad Autónoma de Buenos Aires“). With more than 1,000,000 reported installations. This application helps individuals move around Buenos Aires city by finding public transport. It provides directions and transportation options including bus, subway, train, car, bike, or foot.
Application “BA Cómo Llego” as advertised in the Google Play Store. Source: Google Play Store. Date: 2019-04-02.
The application in Android requests the following permissions according to Google Play Store:
Location (network based, and precise location via GPS)
Photos/Media/Files
Storage
Wi-Fi information
Other:
receive data from Internet
view network connections
full network access
prevent device from sleeping
read Google service configuration,
Location permissions are also explicitly requested when installing in both, Android and iOS.
INFORMATION LEAKED
After successfully installing the application, the user is prompt with two key search fields: ‘From’ and ‘To’, where the user should type origin and destination to find possible routes. When the user starts typing, the application generates an HTTP request sending the partial search to the servers. Note that a minimum of 3 characters should be typed for the request to take place. As the user continues typing, more requests are being made, almost character by character. All the data is transferred in clear text over the network. The first request can be observed in detail in Figure 1, while the series of requests made by the user while typing can be seen in Figure 2.
Figure 1 - All information is sent in clear text. As the user types in the application, the partial text typed is sent to the server to retrieve possible matching locations. This Figure shows the partial text “Thi” being sent. It also shows that the complete HTTP request is not encrypted and therefore anyone with access to the traffic can see what you type.
Additionally, Figure 1 shows how the developers dedicated a special HTTP header for reporting the application that generated the request. In this case: ar.gob.buenosaires.comollego. In the answer, it is possible to observe the results of the partial search in JSON format. This will be populated with results when the written address matches something on the database.
Figure 2 - As the user of “BA Cómo Llego” types, the information is sent in clear text over the network and letter by letter. This leaks not only what you search, but it opens the possibility to use keystroke dynamic technics to know who you are.
As shown in Figure 2, each request sends the text typed by the user in real time. More importantly each letter typed is sent in a new request which makes it possible to analyze the behavior of the user and its profile. The analysis of typing patterns is known as keystroke dynamics and it is possible to use it to profile who the user is. Because the content is unencrypted, this data is available to anybody with access to this traffic.
There also seems to be a bug on the application, as it is generating requests for both “buscar?” and “/buscar/?“, causing the application to be even more noisy with your input text. Figure 3 illustrates this error. This bug also means that the application is using more than double the data bandwidth of your phone compared to what it may use without this bug.
Figure 3 - A bug on the application causes it to generate two requests with the same text to different resource locators. This means that the app uses more than double the data bandwidth of your phone that it should.
LOCATION LEAKING ON ANDROID APPLICATION
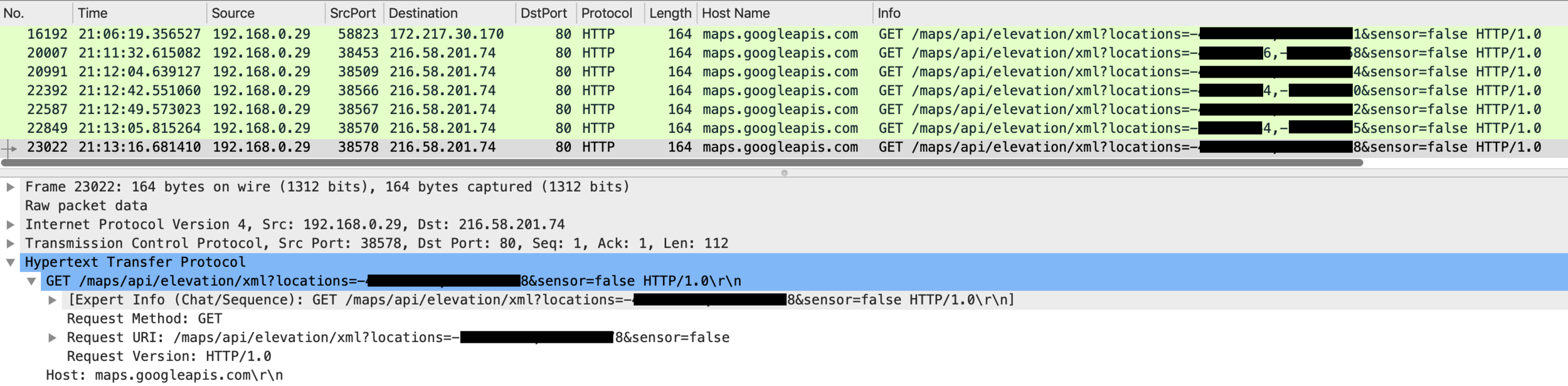
There are two types of location leaking on “BA Cómo Llego”. The first one is about the locations the user is interested in, which is collected by knowing what is typed on the destination and origin of the search fields. The second one is much more important and is the application leaking your exact current location by sending the GPS coordinates in clear text. Your exact location is sent even when the text typed into the “To:” and “From:” fields is not your current location. Figure 4 shows this problem. These requests were triggered when the user consulted the interactive map embedded on the application.
Figure 4 - The application leaks the exact GPS location of the user using unencrypted requests. Even when the user did not search From or To this location.
Figure 5 - Response to the Google APIs location request. It shows how Google actually banned the requests.
In Figure 4 there are several aspects to pay attention to:
The application is using Google Maps API to retrieve data based on the current location.
The protocol used is HTTP 1.0.
Google APIs generally uses HTTPS by default, but these requests do not use encryption.
If we take a look at the response of one of these requests in Figure 5 we can see how Google has blocked them, and it’s actually forbidding the application of making any more requests. This means that the owners of the application are not testing it and are not aware that Google is blocking them. More over, there is no need now to send the GPS location anymore.
Note: The location leaking has only been observed on the Android version of the “BA Cómo Llego” application. This leak do not happen on the iOS version tested at this moment.
CONCLUSION
If you are an individual at risk because of the type of work you do, or the people you help, it is important to understand that any tiny piece of data that is leaked may put you at risk. We carry mobile phones everywhere we go, and it is important to understand that they may put us at risk. We recommend uninstalling “BA Cómo Llego” and using more mainstream transportation apps such as Google Maps that will ensure a minimum level of security.