Update 2019-06-03: On May 6, 2019 the management of “Moovit” application contacted us and ensured that the issues will be fixed in a new versions of the application by the end of May. Both Android and iOS were not fixed and the vulnerabilities remain.
SUMMARY
In this blog post we report important issues found on the public transport application “Moovit” for Android and iOS. Our analysis focused only in the network traffic generated by these applications while used by normal users. In summary, the issues found are:
What you type in the destination and origin field is leaked in plain text. Anyone with access to the traffic can know what you type in real time.
Suggestion of partial searches are leaked in plain text. Anyone with access to the traffic can know potential places that you are searching for.
The chosen origin and destination are leaked in plain text. Anyone with access to the traffic can know the potential route you will be taking.
Every character typed generates a new request, leaking not only what you type but how you type it. Anyone with access to the traffic may analyze who you are.
The iOS version of the application leaks your GPS location to the Open Weather Map. Anyone with access to the traffic can know where you are.
The username and email address of the user is leaked in plain text by a response of the Moovit server. Anyone with access to the traffic can know your email address and know this traffic belongs to you. This is only in the iOS version of Moovit.
This affects iOS application version 5.31.0, and Android application versions 5.30.0.403 & 5.31.0.405.
We have reached out Moovit via email to four different addresses and also via Twitter. We haven’t received any response or acknowledgement to this date.
ABOUT THE APPLICATION
“Moovit” is transport application designed to provide users with information on travel routes whether by car, bus, or foot. In their website (www.company.moovit.com/about), the company describes that they have over 400 million users worldwide:
By combining information from public transit operators and authorities with live information from the user community, Moovit offers travelers a real-time picture, including the best route for the journey.
Named Best Local App by Google in 2016, finalist in the Build for Billions category in 2018, and one of Apple’s Best Apps of 2017, Moovit launched in 2012 and now has over 400 million users.
Moovit amasses up to five billion anonymous data points a day to add to the world’s largest repository of transit data. The data gathering is aided by Moovit’s network of more than 550,000 local editors called “Mooviters.” These passionate users help map and maintain local transit information in cities that would otherwise be unserved. Mooviters account for 70 percent of the hundreds of cities Moovit opens every year and make Moovit the Wikipedia of Transit.
Figure 1 - Application “Moovit” as advertised in the Google Play Store. Source: Google Play Store. Date: 2019-04-11.
According to the information from Google Play Store, the application requests the following permissions:
Identity: find accounts on the device
Contacts: find accounts on the device
Location: approximate location (network-based), precise location (GPS and network-based)
Photos/Media/Files: read the contents of your USB storage, modify or delete the contents of your USB storage
Storage: read the contents of your USB storage, modify or delete the contents of your USB storage
Wi-Fi connection information: view Wi-Fi connections
Other: receive data from Internet, view network connections, pair with Bluetooth devices, full network access, run at startup, draw over other apps, use accounts on the device, control vibration, prevent device from sleeping, read Google service configuration, view network connections, full network access, use accounts on the device, control vibration, prevent device from sleeping.
INFORMATION LEAKED
After opening the application, there is an option to search for a destination. When the user selects a destination, the application proposes several routes that the user can choose from. After selecting a specific route, the application navigates the user to the desired location.
GPS location to the Open Weather Map (iOS)
For iOS users, the information starts leaking the moment the application is opened. The exact GPS location and a unique ID is sent in plain text over HTTP to the Open Weather Map API. Moovit is using Open Weather Map API to provide information about alerts or weather. Note that the request fails, as Open Weather Map has blocked the account due to exceeding requests of the subscription. Also, the GPS location of the general area is also leaked in the response by the server.
Figure 2 - The application leaks the exact GPS location of the user using unencrypted requests to Open Weather Map. Only in the iOS version of Moovit.
Origin and Destination Text Searches
While the user is writing in the destination field, the entire input is leaked together with the suggestions that are being displayed as the user types. The same occurs with the origin location, if the user searches for an address. The GPS location when the ‘current location’ option is selected is not leaked.
Figure 3 - The information entered in the origin or destination fields is sent in clear text. As the user types in the application, the partial text typed is sent to the server to retrieve possible matching locations. This Figure shows the text “this should not happen” being sent. It also shows that the complete HTTP request is not encrypted and therefore anyone with access to the traffic can see what you type.
Suggestion Based on Partial Searches
As the user types, the application suggests destinations that the user can click on and select. These suggestions are also sent in plain text via HTTP.
Figure 4 - The partial text typed is sent to the server to retrieve possible matching locations, which are sent back by the server unencrypted.
Chosen Origin and Destination Points
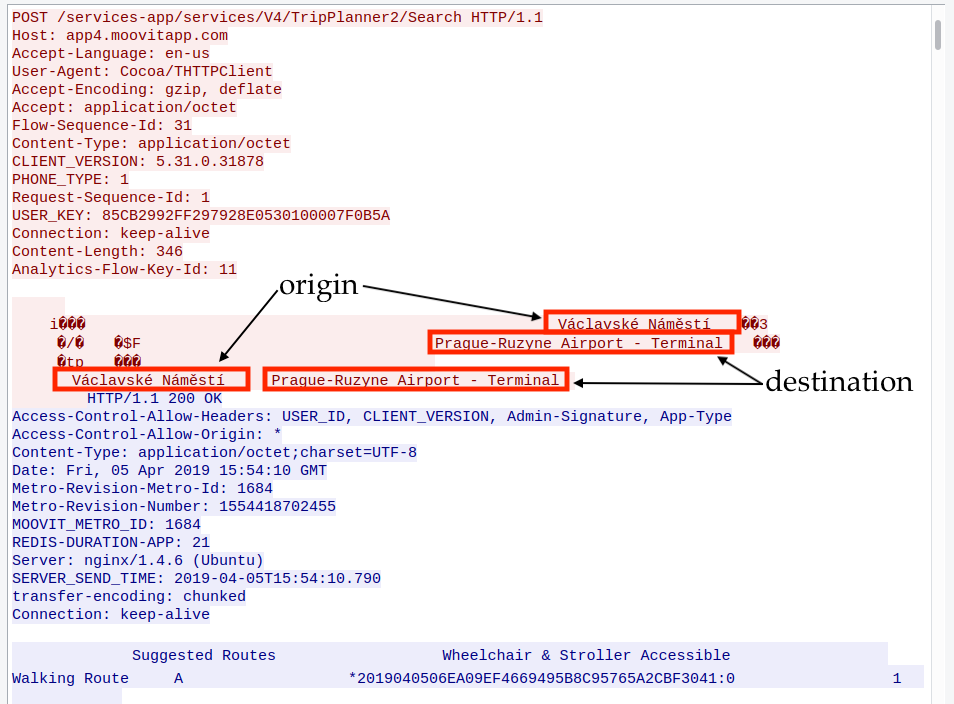
When the user confirms the starting point and the destination. The application sends a request revealing these two points. For example when the user wants to navigate from “Václavské Náměstí” to the Prague Airport, the request looks as follows:
Figure 5 - When the user chooses an origin and destination to see possible routes, these confirmed values (origin and destination) are sent in plain text. Anyone with access to the traffic can know where are you going and which will be your starting point.
What The User Types & Typing Behavior
When the user types the application generates requests with the partial searches to retrieve data. Each request sends the text typed by the user in real time. Each letter (or group of letters if the user types fast) is sent in a new request which makes it possible to analyze the behavior and profile of the user. The analysis of typing patterns is known as keystroke dynamics and it is possible to use it to profile who the user is. Because the content is unencrypted, this data is available to anybody with access to this traffic. The following series of screenshots illustrate this point.
Figure 6 - As the user of “Moovit” types, the information is sent in clear text over the network and letter by letter. This leaks not only what you search, but it opens the possibility to use keystroke dynamic technics to know who you are. This figure shows the user starting to type the letter ‘a’.
Figure 7 - This figure shows the user starting to type the letter ‘airp’.
Figure 8 - This figure shows the user starting to type the letter ‘airpo’.
Figure 9 - This figure shows the user starting to type the letter ‘airport’.
Username And Email Address of the User
Moovit has the option to register or login to sync data among different devices, save favourite locations, and other functionalities. We discovered that the username and email address of the user are leaked in plain text, but not by the client, this time by the server.
Figure 10 - If the user registers and logs in in the Moovit application, its username and email address are sent back from the server in plain text over the network. Anyone can use this information to link this traffic to your real persona.
Lastly, other information about the mobile device is leaked by the mere fact of using HTTP. Information that can be known due the lack of encrypted communications include device type, language settings, application version, and others.
CONCLUSION
Both versions of the Moovit application leak personal data such as location information, unique ID or user’s email (only in iOS). A potential adversary can exploit this information to identify, track and find a targeted victim. The unique IDs also help unequivocally identify user’s data in large amounts of network traffic, making user specific surveillance much easier.
If you are an individual at risk because of the type of work you do, or the people you help, it is important to understand that any tiny piece of data that is leaked may put you at risk. We recommend uninstalling Moovit app and using a different application such as Google Maps which encrypts the content sent to and from the phone.
Stay safe.